Dan Xu
Multinational companies and foreign-invested companies are required to regularly transfer personal information (such as client information, employee information, etc.) to their overseas headquarters for business and management requirements. Under this scenario of data processing, entities in China who will provide the personal information overseas, as processors of personal information under the Personal Information Protection Law (“PIPL”), should meet the legal requirements set out in the PIPL and the relevant regulations.
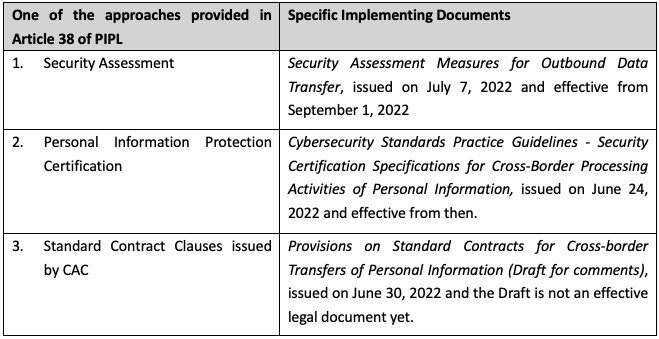
Article 38 of the PIPL provides three basic requirements that the relevant entities in China shall meet before they provide personal information outside of China: (1) to pass a security assessment (the “Security Assessment”) organized by the Cyber Administration of China (“CAC”); (2) to be certified by professional agencies for protection of personal information (the “Certification”); and (3) to enter into a contract with the overseas receiving party per the standard contract issued by CAC (“Standard Contract Clauses”).
After the PIPL came into effect, due to the lack of effective legal instruments providing implementation rules of Article 38 of PIPL, it had been a while whereby companies have no specific and effective operational guidelines to follow for their cross-border transfer of personal information.
Recently, CAC and the Secretariat of the National Information Security Standardization Technical Committee have issued a series of documents which provides specific rules companies should take to meet the requirements set out in Article 38 of PIPL.
We made a list of the correspondence between Article 38 of PIPL and the specific implementing documents, and organized the table as follows:
1. Circumstances where companies shall conduct a Security Assessment
According to the provisions of the Security Assessment Measures for Outbound Data Transfer, if a company processes data up to a certain amount or provides certain types of data to foreign receiving parties, the company shall apply for the Data Security Assessment organized by CAC through the provincial departments of CAC.
The specific circumstances where companies shall conduct a security assessment include: (1) where the company provides critical data abroad; (2) where the company is a key information infrastructure operator or the company processing the personal information of more than one million individuals provides personal information abroad; (3) where the company has provided personal information of 100,000 individuals or sensitive personal information of 10,000 individuals in total abroad since January 1 of the previous year.
2. Procedures and materials necessary for a Security Assessment
Companies shall first carry out a self-assessment regarding the risks of data cross-border transfer before applying for the Security Assessment arranged by CAC. It is worth noting that Articles 55-56 of PIPL also require companies to conduct personal information protection Prior Impact Assessments (“PIA”) before providing data abroad. Compared with the PIA in PIPL, the self-assessment specified in Security Assessment Measures for Outbound Data Transfer is more comprehensive and detailed.
In addition, companies and their overseas receiving parties shall agree on the terms and conditions to provide the overseas receiving party’s obligations and responsibility for data security protection.
When applying for the Security Assessment to CAC, companies should submit an application form, a self-assessment report on risks of data cross-border transfer, agreements concluded by the Chinese entities and the overseas receiving party and other materials required for the security assessment. If the CAC considers it unnecessary for the company to conduct the Security Assessment, it will issue a notice of non-acceptance to the company, and the company can carry out data cross-border transfer activities through other approaches mentioned above (e.g. the Certification or Standard Contract Clauses).
CAC will complete the Security Assessment within 45 working days from the date when the written receipt notice is issued; if the situation is complex or requires more materials to be submitted by the company, the CAC may appropriately extend and inform the company of the expected extended time. The company that passes the Security Assessment will receive written notification from CAC, after which the company may conduct data cross-border transfer activities in accordance with whatever is applied for.
The result of the Security Assessment is valid for two years from the date when the assessment result has been issued. If the purpose and mode of cross-border data transfer and the situation of the overseas receiving party change, the company shall apply for a new Security Assessment.
3. The content of the security assessment
After the company submits the application materials, the CAC will focus on assessing the risks that data cross-border transfer may bring to national security, public interests, and the legitimate rights and interests of individuals or organizations, mainly including:
- The legality, legitimacy and necessity of the purpose, scope, and method of the outbound data transfer;
- The impact of the data security protection policies and laws and the cybersecurity environment of the country or region where the overseas receiving party is located on the security of data to be transferred, and whether the data protection level of the overseas receiving party meets the requirements of the laws and administrative regulations of the China and mandatory national standards;
- The scale, scope, types and sensitivity of data to be provided abroad, and the risks that the data may be tampered with, destroyed, divulged, lost, transferred, illegally obtained or illegally used during and after the data is provided abroad;
- Whether data security and personal information rights and interests can be fully guaranteed;
- Whether the legal documents to be concluded by the data processor and the overseas receiving party have fully agreed on the responsibilities and obligations of data security protection;
- Whether the parties are compliant with Chinese laws, administrative regulations and departmental rules.
Conclusion
Before providing data outside of China, Companies are recommended to first have an internal assessment to check whether a CAC assessment is required i.e. to check if it falls into any of the circumstances as mentioned above. Based on such an assessment, companies may further decide which route they should choose to provide the data outside of China and what compliance steps they should take to meet the specific requirements under a different route.
DaWo Law Firm has extensive experience in personal information protection and data compliance. Please feel free to contact us if you have any questions.


